Threat actors behind the infamous TrickBot malware have been linked to a new ransomware strain named “Diavol,” according to the latest research.
Diavol and Conti ransomware payloads were deployed on different systems in a case of an unsuccessful attack targeting one of its customers earlier this month, researchers from Fortinet’s FortiGuard Labs said last week.
TrickBot, a banking Trojan first detected in 2016, has been traditionally a Windows-based crimeware solution, employing different modules to perform a wide range of malicious activities on target networks, including credential theft and conduct ransomware attacks.
Despite efforts by law enforcement to neutralize the bot network, the ever-evolving malware has proven to be a resilient threat, what with the Russia-based operators — dubbed “Wizard Spider” quickly adapting new tools to carry out further attacks.
Diavol is said to have been deployed in the wild in one incident to date. The source of intrusion remains unknown as yet. What’s clear, though, is that the payload’s source code shares similarities with that of Conti, even as its ransom note has been found to reuse some language from Egregor ransomware.
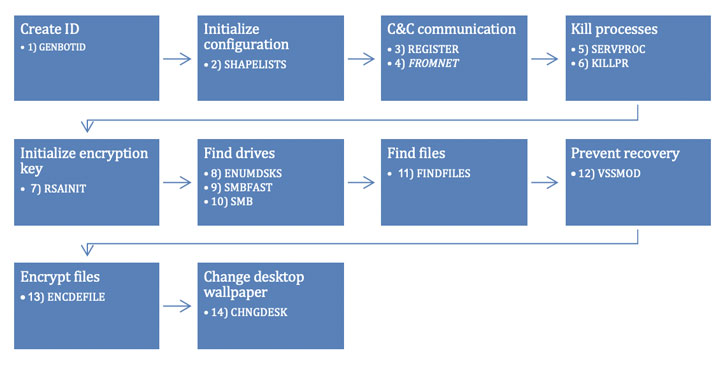
“As part of a rather unique encryption procedure, Diavol operates using user-mode Asynchronous Procedure Calls (APCs) without a symmetric encryption algorithm,” the researchers said. “Usually, ransomware authors aim to complete the encryption operation in the shortest amount of time….